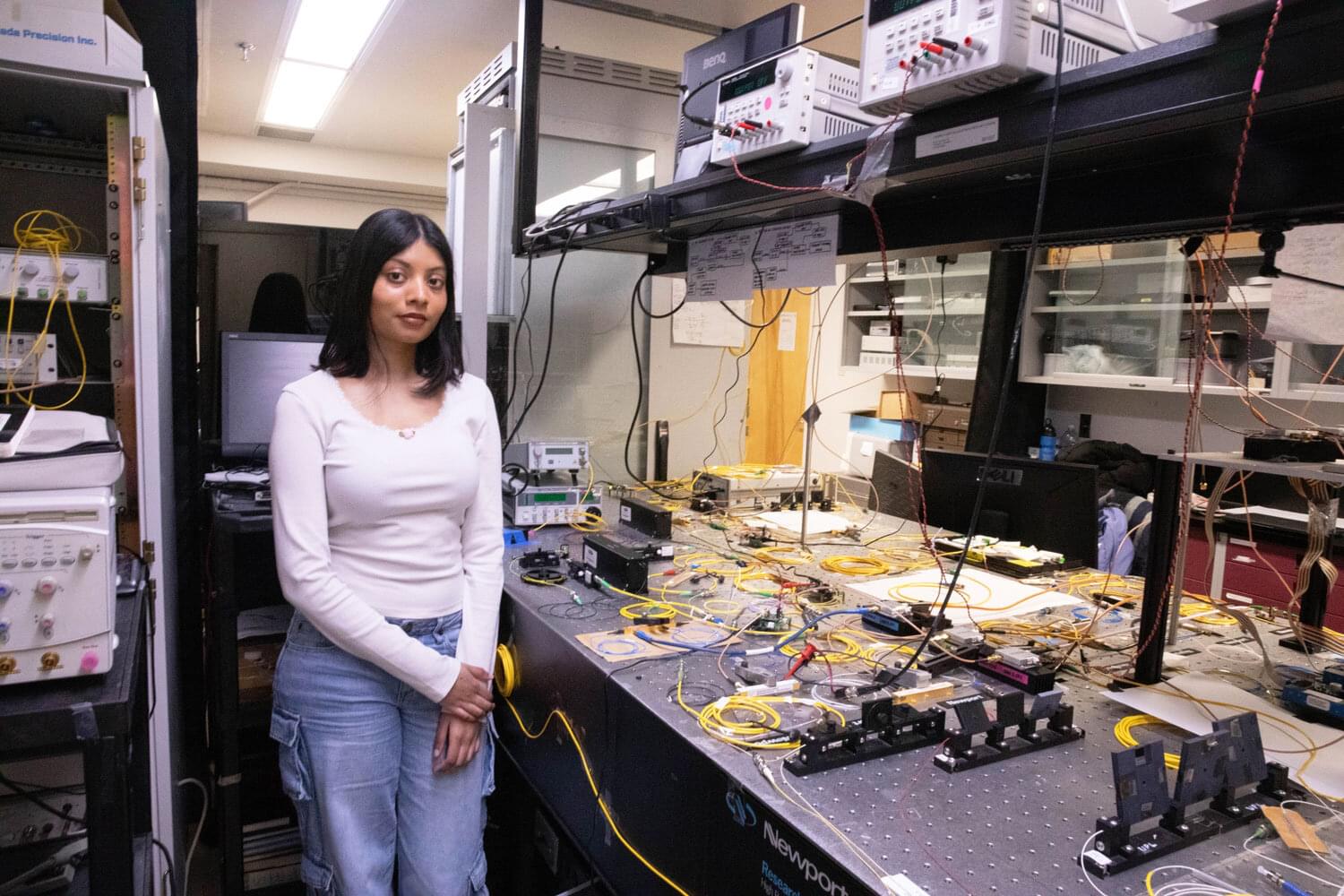
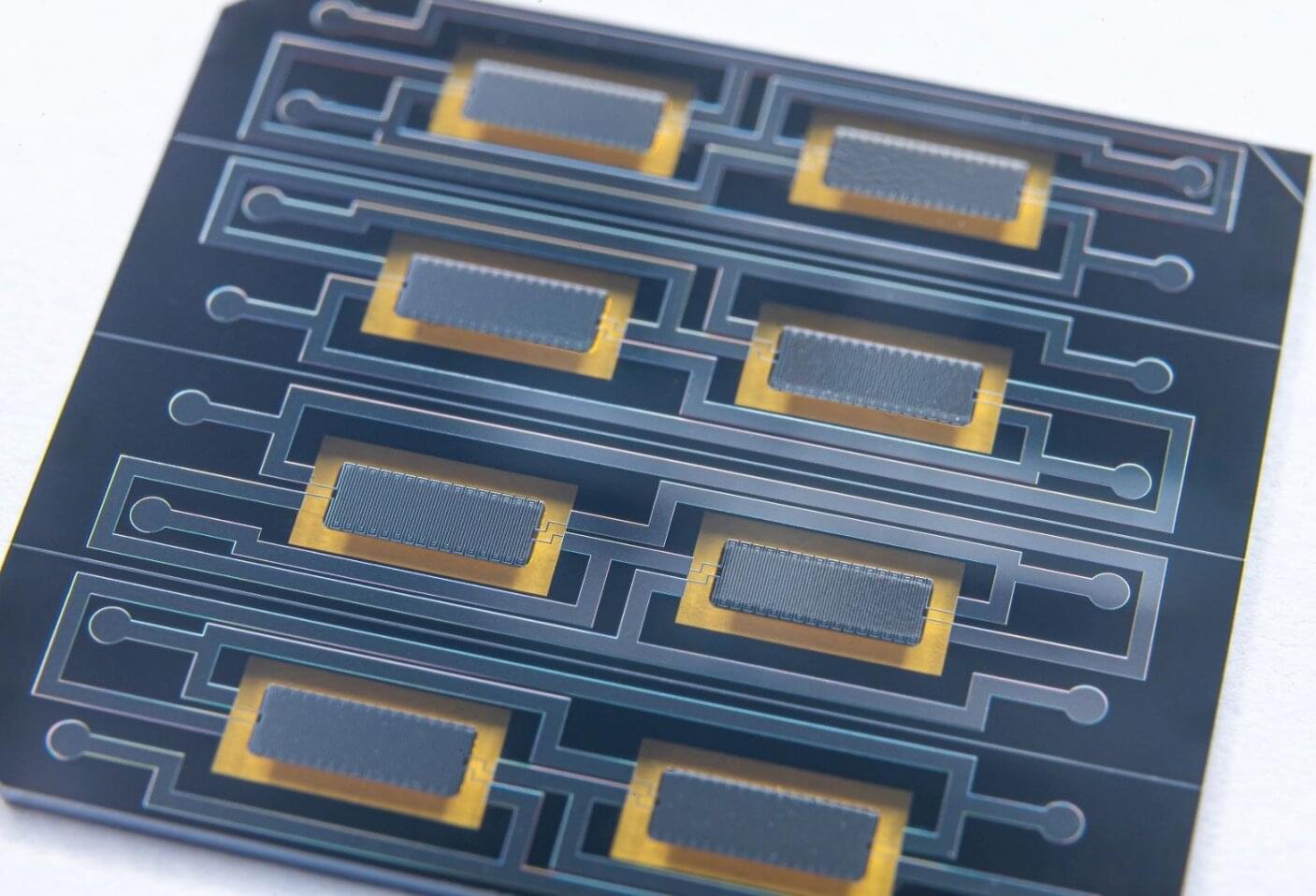
Researchers have successfully demonstrated the UK’s first long-distance ultra-secure transfer of data over a quantum communications network, including the UK’s first long-distance quantum-secured video call.
The team, from the Universities of Bristol and Cambridge, created the network, which uses standard fiber-optic infrastructure, but relies on a variety of quantum phenomena to enable ultra-secure data transfer.
The network uses two types of quantum key distribution (QKD) schemes: “unhackable” encryption keys hidden inside particles of light; and distributed entanglement: a phenomenon that causes quantum particles to be intrinsically linked.