Jul 4, 2016
China to launch ‘hack-proof’ quantum satellite next month
Posted by Karen Hurst in categories: computing, encryption, quantum physics, satellites
Get ready.
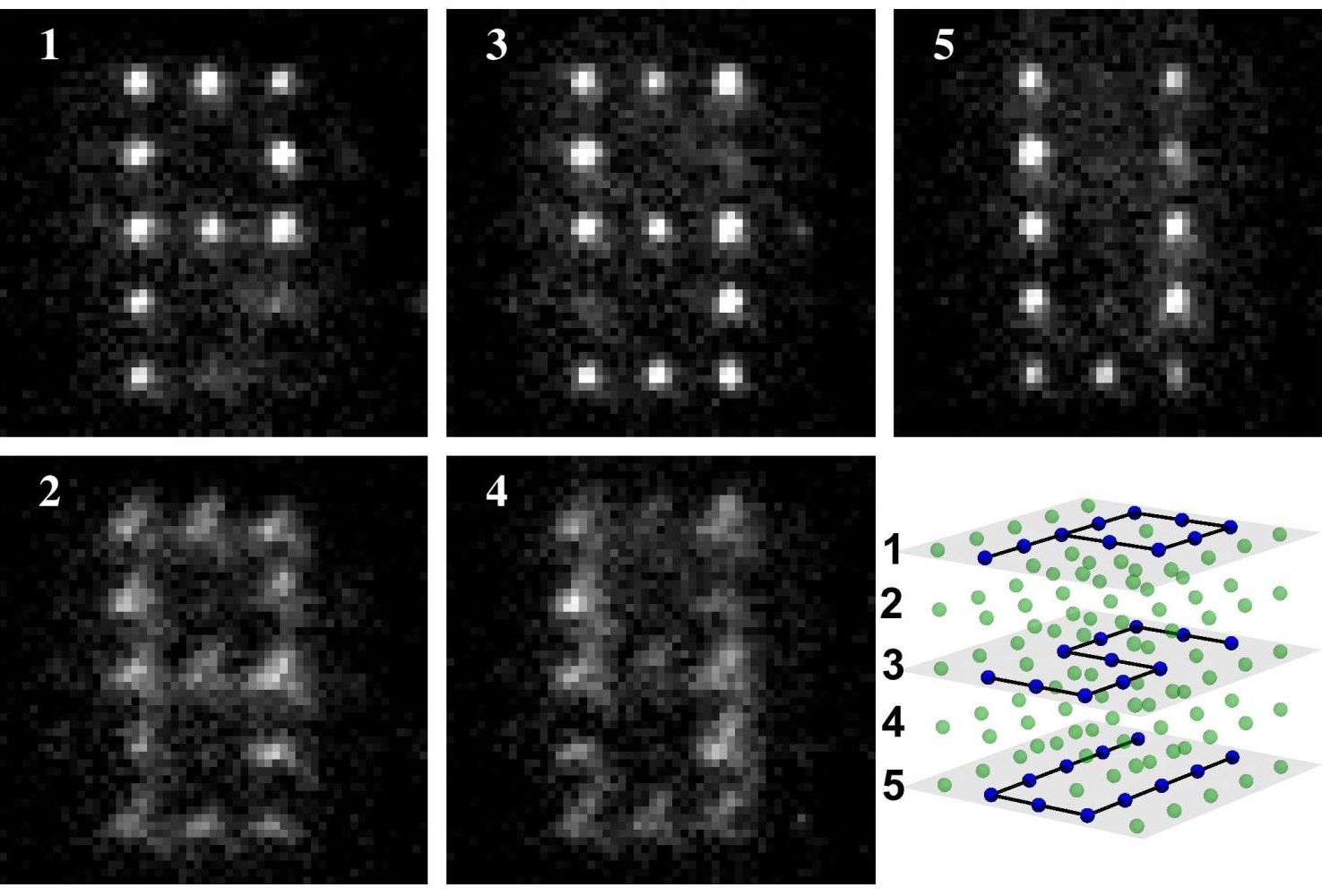
China will launch the world’s first quantum satellite next month to demonstrate a series of advanced technologies such as hacker-proof communications and quantum teleportation.
Ground testing and quality checks on the satellite had finished at the Chinese Academy of Sciences, and it would depart for the Jiuquan Satellite Launch Centre in Inner Mongolia early this month for a launch aboard a Long March 2D rocket in the middle of next month, according to a report on the central government’s website posted on Friday.
Continue reading “China to launch ‘hack-proof’ quantum satellite next month” »