Energy efficient IoT — proven to reduce energy usage by 50% via new technique for compressing the computations of encryption and decryption operations known as Galois field arithmetic operations.
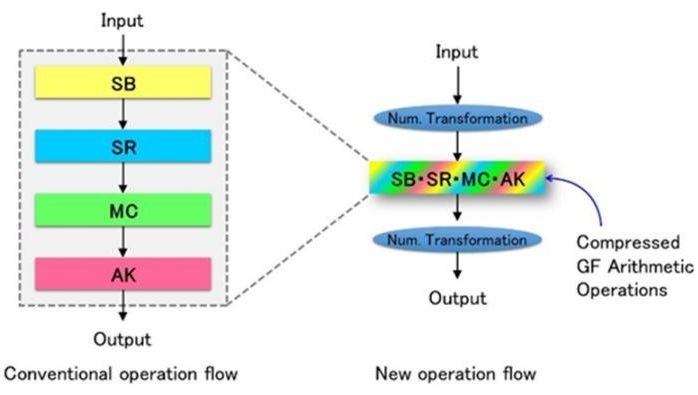
Our research group has discovered a new technique for compressing the computations of encryption and decryption operations known as Galois field arithmetic operations, and has succeeded in developing the world’s most efficient Advanced Encryption Standard (AES) cryptographic processing circuit, whose energy consumption is reduced by more than 50% of the current level. With this achievement, it has become possible to include encryption technology in information and communication technology (ICT) devices that have tight energy constraints, greatly enhancing the safety of the next-generation Internet of Things (IoT). This result was announced on August 19, 2016 during the Conference on Cryptographic Hardware and Embedded Systems 2016 (CHES 2016) hosted by the International Association for Cryptologic Research (IACR) in Santa Barbara, USA.
It is currently very common to exchange important personal or financial information over the Internet through ICT devices. Cryptographic techniques are used inside these devices to protect important information. In next-generation networks such as the IoT, which has attracted attention in recent years, it is expected that myriad devices will be connected to the network. Hence, it will be necessary to have built-in encryption technology in these connected devices to prevent malicious attacks. However, many battery or cell-driven devices with tight energy constraints are also included in the IoT and running energy-consuming encryption processes on these is a big challenge. One of the most widely used international standard encryption methods is AES. Since this is used in areas such as wireless LANs, it is very important for practical reasons to design energy-saving AES cryptographic processing.
Continue reading “World’s most efficient AES crypto processing technology for IoT devices developed” »