Jan 18, 2023
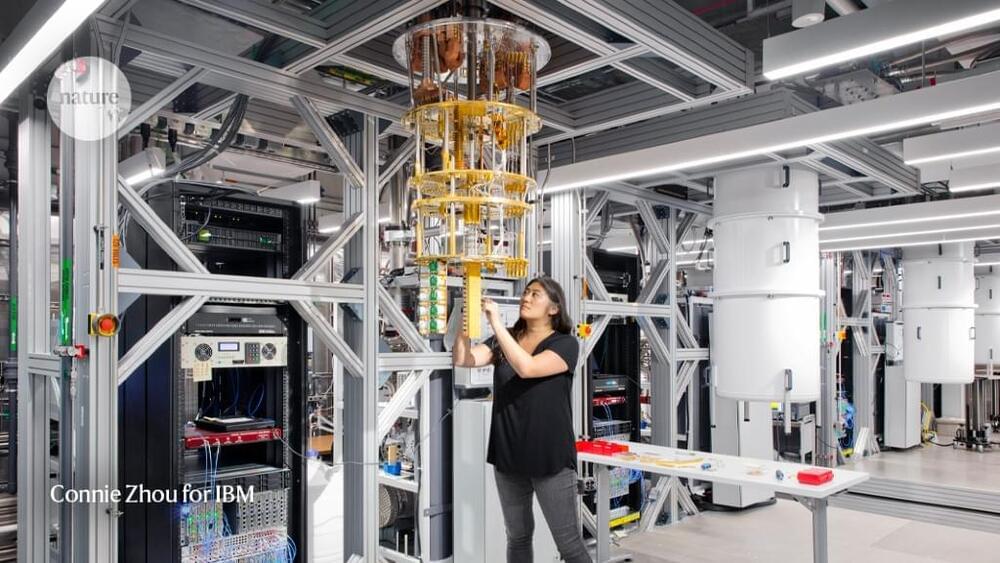
IBM: Quantum computing poses an ‘existential threat’ to data encryption
Posted by Paul Battista in categories: business, computing, encryption, existential risks, quantum physics, security
Check out all the on-demand sessions from the Intelligent Security Summit here.
For years, encryption has played a core role in securing enterprise data. However, as quantum computers become more advanced, traditional encryption solutions and public-key cryptography (PKC) standards, which enterprise and consumer vendors rely on to secure their products, are at serious risk of decryption.
Today, IBM Institute for Business Value issued a new report titled Security in the Quantum Era, examining the reality of quantum risk and the need for enterprise adoption of quantum-safe capabilities to safeguard the integrity of critical applications and infrastructure as the risk of decryption increases.