Biohacking raises a host of ethical issues, particularly about data protection and cybersecurity as virtually every tech gadget risks being hacked or manipulated. And implants can even become cyberweapons, with the potential to send malicious links to others. “You can switch off and put away an infected smartphone, but you can’t do that with an implant,” says Friedemann Ebelt, an activist with Digitalcourage, a German data privacy and internet rights group.
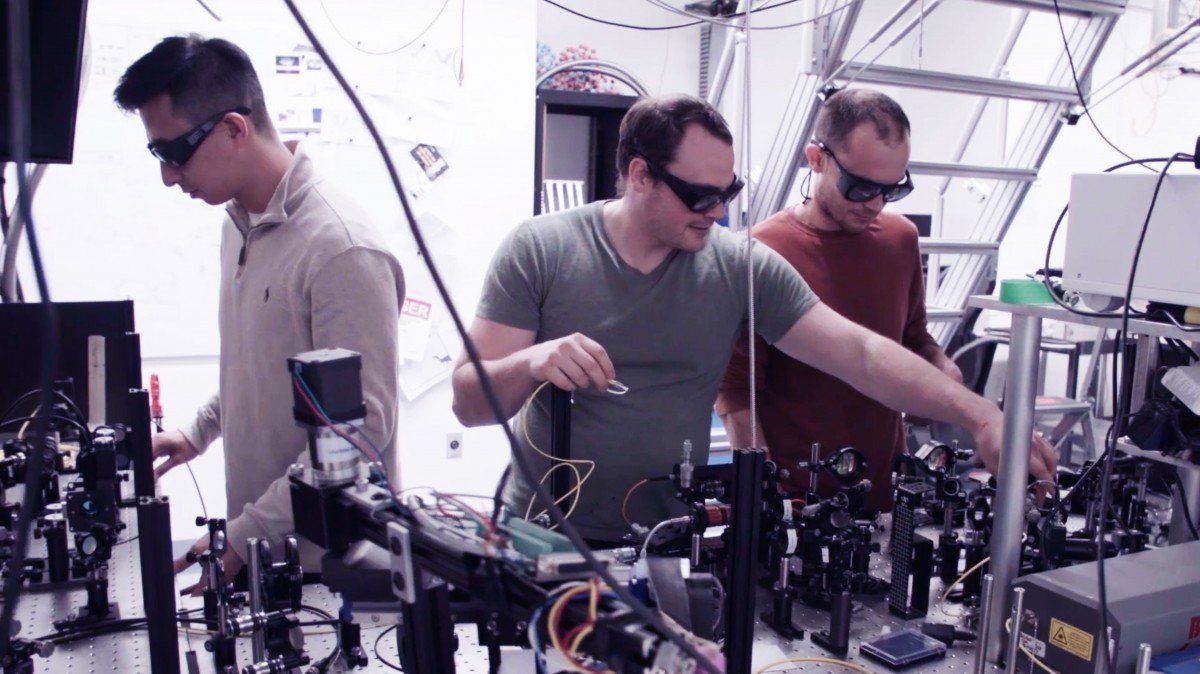
Patrick Kramer sticks a needle into a customer’s hand and injects a microchip the size of a grain of rice under the skin. “You’re now a cyborg,” he says after plastering a Band-Aid on the small wound between Guilherme Geronimo’s thumb and index finger. The 34-year-old Brazilian plans to use the chip, similar to those implanted in millions of cats, dogs, and livestock, to unlock doors and store a digital business card.
Kramer is chief executive officer of Digiwell, a Hamburg startup in what aficionados call body hacking—digital technology inserted into people. Kramer says he’s implanted about 2,000 such chips in the past 18 months, and he has three in his own hands: to open his office door, store medical data, and share his contact information. Digiwell is one of a handful of companies offering similar services, and biohacking advocates estimate there are about 100,000 cyborgs worldwide. “The question isn’t ‘Do you have a microchip?’ ” Kramer says. “It’s more like, ‘How many?’ We’ve entered the mainstream.”
Continue reading “Biohackers Are Implanting Everything From Magnets to Sex Toys” »