Dec 14, 2018
Facebook’s latest privacy scandal: The private photos of millions of users were accidentally shared with 1,500 apps
Posted by Michael Lance in category: cybercrime/malcode
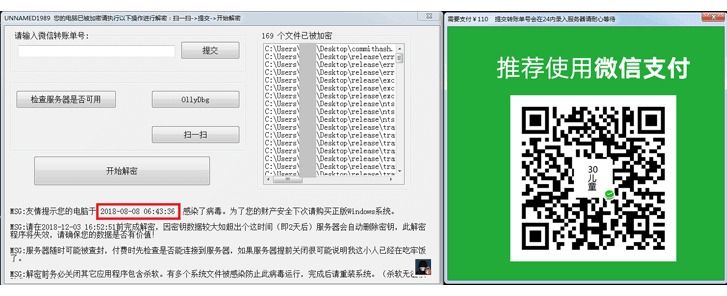
“We’re sorry this happened,” Facebook said in a statement after disclosing yet another privacy failing.
Facebook said on Friday in a developer-focused blog post that it had discovered a nasty bug in its photo software.
The bug allowed authorized app programmers to access photos that people had uploaded to Facebook but not publicly shared, as well as those posted on Facebook’s Marketplace software or Facebook Stories, the post said.