Aug 4, 2019
The U.S. Spy Hub in the Heart of Australia
Posted by Richard Christophr Saragoza in categories: security, surveillance
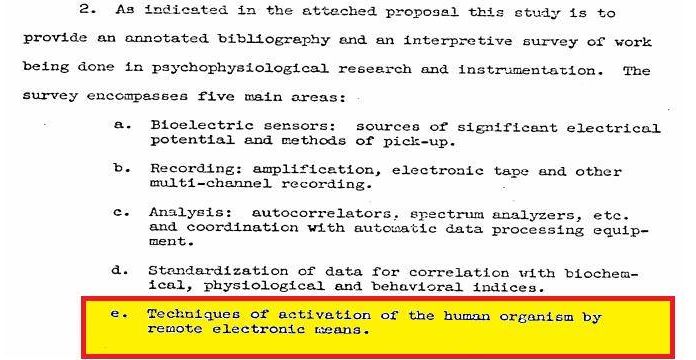
A short drive south of Alice Springs, the second largest population center in Australia’s Northern Territory, there is a high-security compound, code-named “RAINFALL.” The remote base, in the heart of the country’s barren outback, is one of the most important covert surveillance sites in the eastern hemisphere.