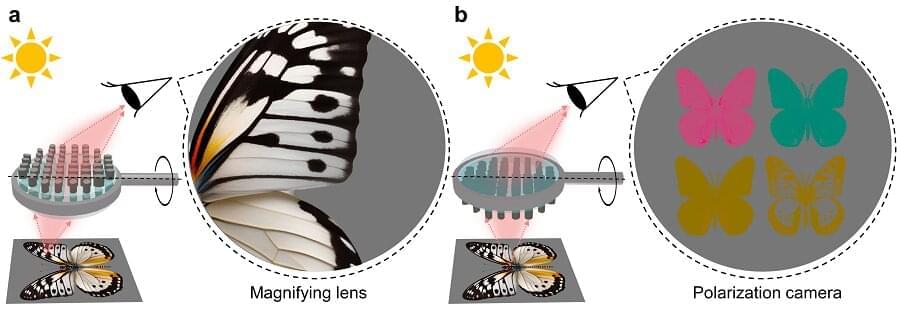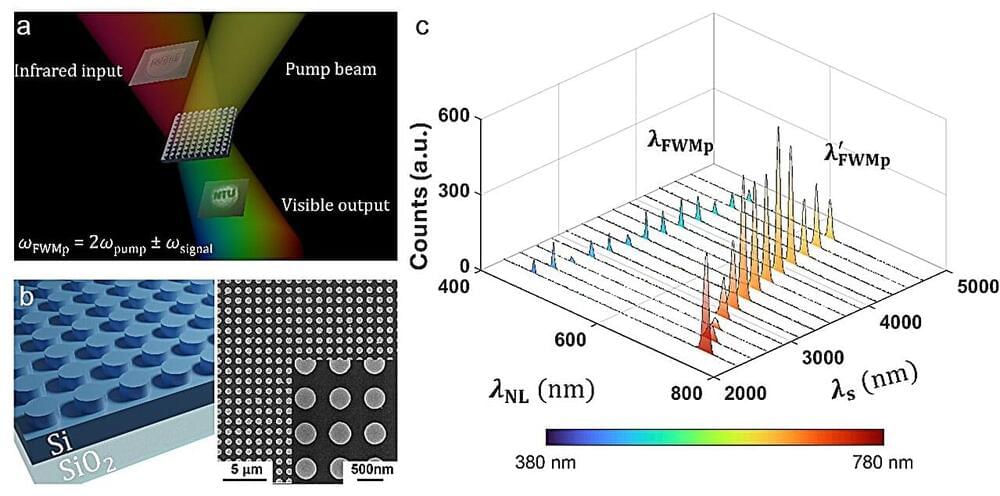
While infrared cameras are valuable tools for enhanced vision, food and plant quality control, security, etc, today’s cameras often face significant drawbacks. For instance, they are bulky and power-hungry, requiring cooling systems that limit their functionalities.
More importantly, current semiconductor-based technology used in the cameras only captures a narrow band of the infrared spectrum based on the absorption band of the semiconductor detector. This means that every application would need a separate camera.
“Due to the complications of today’s bulky, power-hungry and expensive infrared imaging technology, we are unlikely to have an infrared camera at home. However, nonlinear frequency conversion, a process that manipulates and translates electromagnetic signals across various frequency regimes, holds a massive potential to revolutionize infrared detection technology,” said Prof Mohsen Ramhami, the leader of Advanced Optics and Photonics Lab, and a UK Research and Innovation Future Leaders Fellow.